As part of our OSINT Fundamentals series, one of our experienced Fivecast Tradecraft Advisors explains the application of the intelligence cycle when conducting an Open-Source Intelligence (OSINT) investigation.
What is the intelligence cycle?
The intelligence cycle is the process that many government and commercial organizations use to organize their workflows when conducting intelligence activities. Even though there are many different intelligence disciplines, variations of this cycle are present across all of them. In this blog, we will broadly discuss each step in the intelligence cycle and contextualize those steps in an open-source intelligence (OSINT) workflow.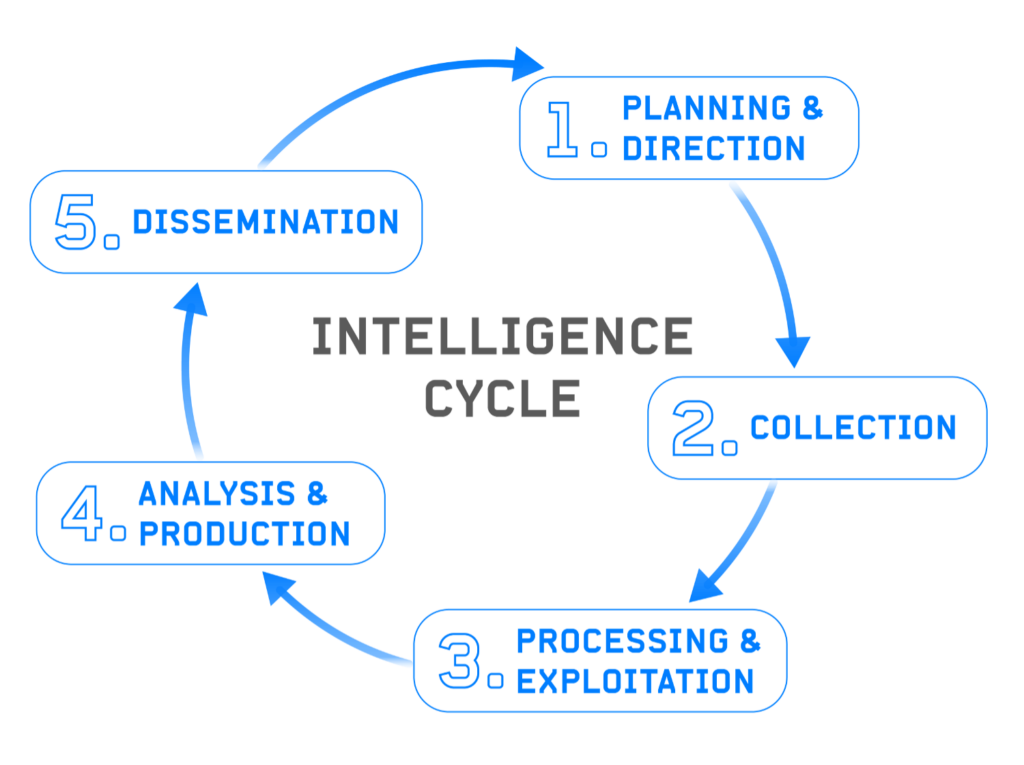
Planning and Direction
The first step of the intelligence cycle is focused on defining intelligence requirements and planning how an operation will be carried out. This process is usually initiated by a commander or team lead when they dictate what information gaps they are trying to fill. The intelligence analysts will then need to develop and bring a plan to a team lead or director for approval. While the overall process for this step in the cycle may be similar across intelligence disciplines (INTs), the intelligence gaps and steps needing to be carried out will vary.
When organizing and planning an OSINT operation, it can be helpful to consider the five W’s (and one H). Who will be conducting the work, and who is the target of collection efforts? What will the type, format, and content of the data collected be? When will collection need to occur so as not to attract additional attention, and what is the timeframe to focus on in terms of collected data? Where should an analyst look for relevant information in terms of sources (news, social media, Dark web, Deep web, etc.)? Why is the information collected essential to the overall mission? And finally, how will the team keep security, access, and archiving considerations in mind when conducting collection activities?
Collection
Once a plan has been developed and approved, analysts can begin carefully collecting OSINT data to fill the intelligence requirements. Collection of the data can often be the longest step of the cycle, as many analysts rely on manual methods to conduct this collection. Management of online footprints, access to sites, and documentation of findings can all be hurdles that slow down the overall process. Depending on where the information of interest is located and how easily it can be accessed, an analyst could spend a fair bit of time collecting and archiving all the relevant data.
Want to learn more about Open-Source Intelligence? Read our Industry Brief: Getting Started with OSINT
Processing and Exploitation
After the data has been collected, it must be processed and exploited accordingly. This could include translating content collected in a foreign language, transcribing audio, and evaluating the reliability of a source of information. At this stage, the data collected needs to be interpreted by an analyst to properly prepare it for incorporation into final products. This may also require additional validation and contextualization of any information collected so that it is framed appropriately.
Analysis and Production
Once the data has been processed, it can be analyzed and prioritized for use in final intelligence products. This often means distilling the information into a digestible, simplified intelligence product that can be briefed or presented to a commander or team lead. At this point in the cycle, OSINT is often integrated or fused with other intelligence to develop a single, more complete product. This is also the step where an analyst may weigh in with insights or commentary to lend expertise and perspective to the intelligence product.
| How Fivecast ONYX can Empower Analysts following the Intelligence Cycle | |
|---|---|
| Planning | Fivecast ONYX allows for analysts and administrators to plan out an operation and organize multiple aspects of the investigation before collection has begun. |
| Collection | Fivecast ONYX provides persistent access to data, security for analyst and agency, and seamless organizing and archiving of data. |
| Processing & Exploitation | Fivecast ONYX standardizes the data so it's all available in one feed (network, activities, media, etc.), enables review of overall behavior of each account for source and content validation, prioritizes content and translates content. |
| Analysis and Production | Fivecast ONYX analyzes media, network, and overall content and provides the analyst with visuals, exporting, and reporting options. |
| Dissemination | Fivecast ONYX works seamlessly with other systems and can easily support production for a variety of formats and distributions timelines with its near real time data collection and analysis. |
Dissemination
The last step of the intelligence cycle sees the final products delivered to the intended audience, typically whoever initiated the first step of the cycle. This step can also include dissemination to a broader audience depending on the intelligence in the reports and the goal of an overall intelligence operation. In the case of OSINT, dissemination of an intelligence product to a wide audience is often a key goal, given the nature of the information is more easily shared across organizations and partner nations. The level of urgency and speed of dissemination depends on the nature of the information being reported; indications and warnings would take a higher priority over a weekly update brief. Evaluation and feedback will likely take place most prominently at this stage of the intelligence cycle but are often observed throughout the other steps as well. Once this step is complete, the intelligence cycle can be repeated for the next product.

