Guest blog from Providence Consulting Group (Providence), a Fivecast partner and provider of risk and protective security services to Australian federal/state government entities, the Department of Defence, and the private sector – including critical infrastructure entities.
In this blog, Marina Maydanov, a Critical Infrastructure Security Practice Lead from Providence Consulting Group shifts the focus from cyber to personnel security and discusses the long-term benefits of designing people-centric Critical Infrastructure Risk Management Programs to mitigate insider threat and protect critical assets, thus bolstering enterprise security.
Cybersecurity is often the focal point of discussion around implementation of the Security of Critical Infrastructure Act 2018 (SOCI Act) and the Security of Critical Infrastructure (Critical infrastructure risk management program) Rules 2023 (Rules) requirements.
Focus on 1s and 0s and cyber incident security controls in your Critical Infrastructure Risk Management Program (CIRMP) is understandable, and required, particularly in the environment of increasing threats from cybercriminals and foreign entities conducting successful cyberattacks.
However, this kind of thinking assumes that cyberattacks come mainly from external ‘threat actors’ outside your organisation, potentially missing the risk coming from insiders with legitimate access to your resources – people, information and material assets. A monocular focus on cybersecurity controls and technology could be a band-aid solution that fails to consider the human-induced threat source of those attacks.
According to the recently released Verizon 2023 Data Breach Investigations Report, 74% of all data breaches include the human element, with people being involved either via error, privilege misuse, use of stolen credentials or social engineering. The Verizon 2023 Report also shows that for critical infrastructure sectors one out of every five data breaches – 20% – intentionally originate from the inside of your organisation!
You might ask what would be the motivation for people who are committed to their work and are loyal to the company to misuse their legitimate access? And start wondering whether your security controls are effective in identifying and managing insider risk.
Insider attacks are often the worst nightmare of security leaders and practitioners because identifying and stopping these kinds of security breaches is so challenging and costly. Since 2021, incidents of insider threats have increased by 44% with the cost per incident constituting US$15.38M (2022 Cost of Insider Threats: Global Report, Ponemon Institute).
personnel security measures
Let’s explore what personnel security measures are required to protect your critical assets and mitigate insider threat. I will also touch on the compliance with a ‘personnel hazard’ requirement of CIRMP where mitigation of malicious and negligent employees or contractors is now a legislative obligation under the Rules.
When talking about insider threat, people often visualise a foreign spy or a Snowden-type of insider who compromises highly sensitive government information. However, insiders and their motivations differ significantly, from someone disgruntled taking your IP when leaving your organisation or being stressed and overworked so unintentionally clicking the phishing link enabling the cyberattack.
The ASIO 2023 Countering the Insider Threat: A Security Manager’s Guide, available through ASIO outreach, defines an insider as ‘a current or former employee or contractor who has legitimate or indirect access to a workplace’s people, information, techniques, activities, technology, assets or facilities’.
There are two types of insiders: unintentional (negligent) and intentional (malicious) insiders. An insider’s reasons for conducting harmful activities, either intentionally or unintentionally, are varied, often complex and, as shown by decades of international research, commonly have more than one motivation for their activity.
Table A: Common motivations of trusted insiders.
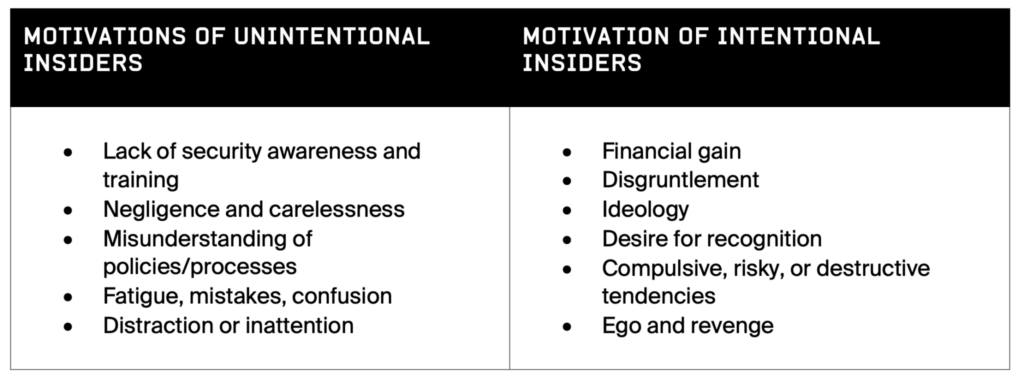
The 2023 Verizon report also revealed that following analysis of last year’s misuse of legitimate access, a shocking figure of 89% of malicious insiders are motivated by financial gain, 13% by disgruntlement, and 5% by espionage.
Lastly, do keep in mind that organisational culture and personnel management processes can foster a working environment conducive to insider threats: employees feel undervalued, unsupported, or treated unfairly.
So, what can be done?
Creating an insider threat program
A well-balanced Insider Threat Program (ITP) as a component of a CIRMP can be seen as an advocate for employee wellbeing and a means for a more productive, engaged, connected, and committed workforce. An ITP also provides risk management for your organisation.
An in-house Workforce Security Risk-Based Screening lies at the heart of an effective ITP and provides an organisation with a level of ongoing assurance around an initial and ongoing suitability of their critical workers to access critical assets.
how to establish an in-house Workforce Security Risk-Based Screening:
1. Identify Critical WOrkers
- Establish a role-based risk assessment process to identify critical positions.
- Conduct a risk assessment of role functions that require access to critical assets or making critical decisions.
- Establish a Register of Critical Workers (critical positions).
2. Pre-employment suitability screening
- Establish eligibility and suitability requirements linked to your organisational risk profile.
- Remember that not all employees need the same level of checks, so invest only where you need to.
- Regularly evaluate your pre-employment screening policies and processes.
3. Establish a cultural norm
- Establish and clearly communicate a norm of behavioural expectation at your workplace.
- Roll out a top-down implementation of security policies.
- Introduce regular tailored security awareness and training programs.
4. Ongoing suitability Assessment
- Establish a process to assess and manage the ongoing suitability of your critical workers.
- Establish reporting, investigation capability and robust monitoring processes.
- Consider the benefits of open-source intelligence platforms, like Fivecast MATRIX, in continuous assessments of publicly available information.
5. Offboarding
- Develop a risk assessment matrix for offboarding of personnel.
- Ensure that separating personnel have their access to resources withdrawn and are informed of any ongoing security obligations.
- Consider notification to relevant third parties and retention of records.
- Open-source intelligence can assist in determining if former employees are inappropriately sharing your information and IP.
Figure B: Open-Source Intelligence covers an array of Insider Threat Program needs